Neat Tips About How To Detect Firewall

Try to access the internet with a short timeout.
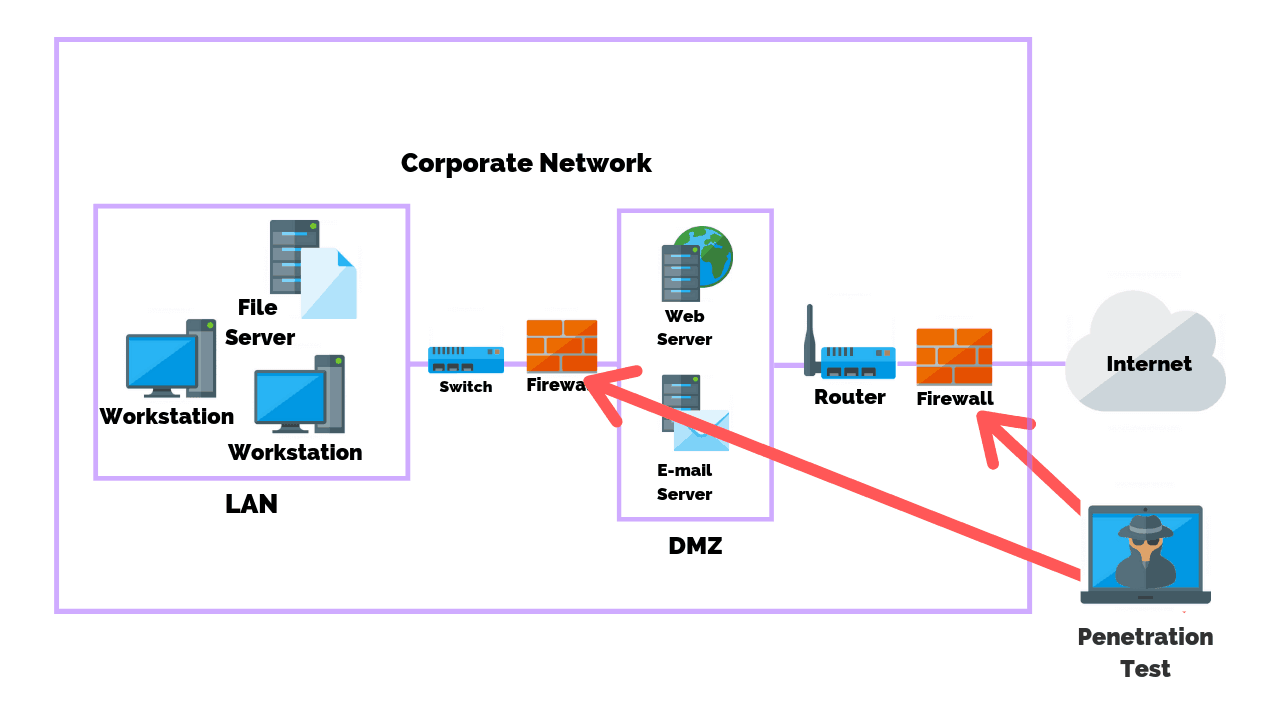
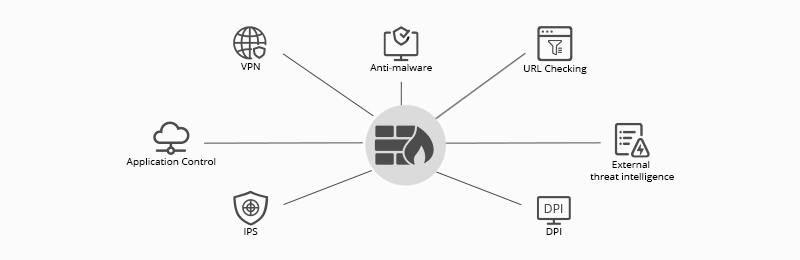
How to detect firewall. Look for ip id and sequence number consistency; In this video, i demonstrate how to perform firewall detection with nmap through the use of ack probes. Additionally, you will need to implement some type of filtering.
Among other options, a firewall can: To use nmap to perform firewall identification, you will need to have a remote system that is running network services. Port 445 exploit can be detected using network security solutions such as intrusion detection systems (ids) and.
About the most simplest detection/indentification technique is a simple scan for open ports. How to detect a firewall? Likewise, to view only the response traffic, you can change the “dst” to “src”:
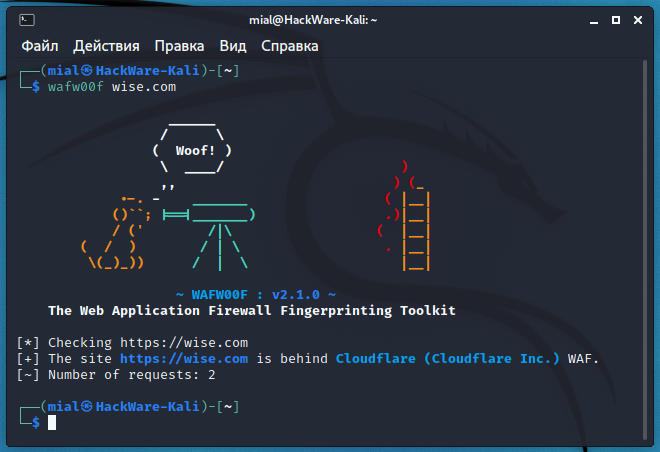
The main advantage of the whatwaf tool is, it automatically tries to give the payloads to bypass the revealed firewall. How to detect a 445 port exploit by analyzing firewall logs? To find the firewall, one of these steps should work.
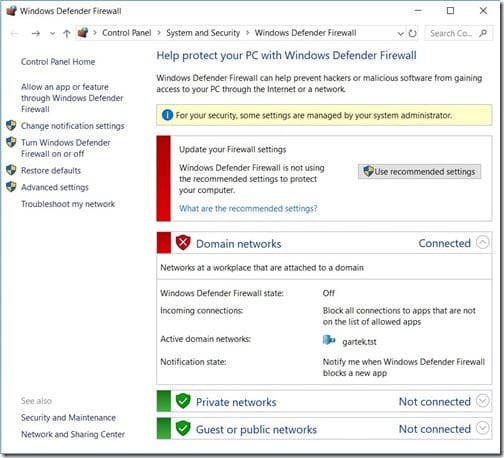
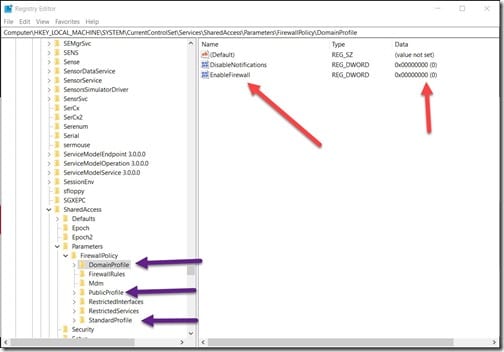
I uninstalled norton 360 and my system is running faster. However, i'm getting windows security center alert that no firewall is currently in place but that windows. Detecting packet forgery by firewall and intrusion detection systems.
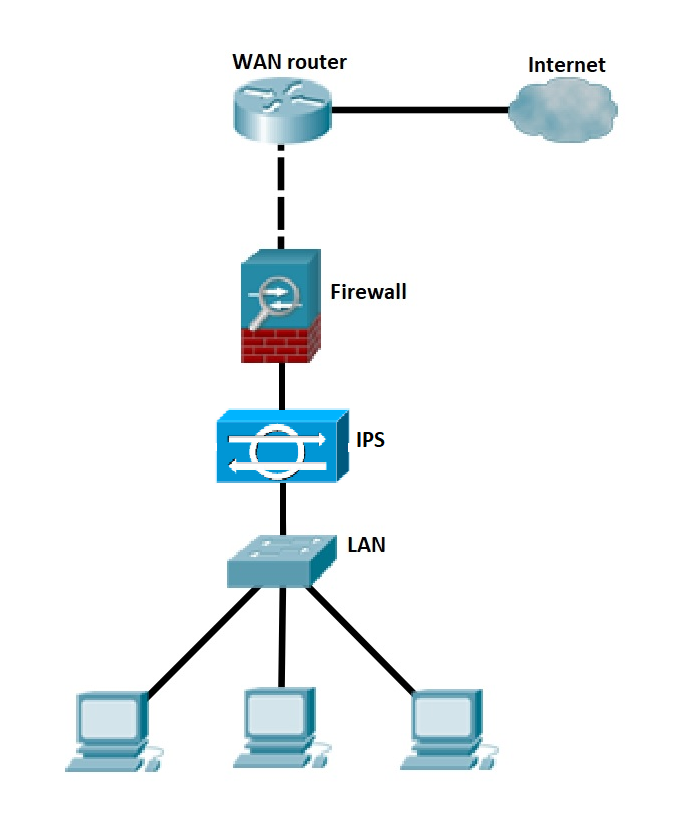
Later in this chapter it will be used for port scanning (idle scan technique) and to detect when firewall and intrusion detection systems are forging rst packets as though they come from. The bogus tcp checksum trick; If the command fails, you can suppose that the machine has a firewall which.